Blockchain technology has gained significant attention in recent years, transforming various industries such as finance, healthcare, and logistics. One of the key components of blockchain technology is hashing, which plays a key role in ensuring data integrity and enhancing security.
Before analyzing blockchain hashing, it is important to understand what blockchain is. At its core, blockchain is a digital ledger that records transactions across a network of computers. Each transaction is grouped into a block, which is then sequentially added to the chain, hence the name “blockchain”.
Each series of blocks contains a set of transactions. These blocks are linked to each other using cryptographic hashes, creating an unalterable chain of information.
Hashing is a cryptographic process of converting certain data into a fixed-size string of characters, known as hash value. The goal of hashing is to create a unique identifier (hash) for a given set of data. The hashing process consists of:
Hashing is used in blockchain for ensuring data integrity and enhancing security within the network.
Each block includes the hash value of the previous block, creating the “chain” of “blocks”. The interdependence of blocks through their hash values makes it almost impossible for an attacker to alter the data of a single block without changing the entire blockchain. How?
Since each block contains a unique hash value, any slight alteration in the data will result in a different hash value, alerting the network of potential tampering attempts.
By creating a unique fingerprint of each block, hashing provides an efficient mechanism for detecting any unauthorized changes to the data, thus maintaining the trust and transparency that are core to the blockchain.
Blockchain hashing adds an extra layer of security to the network. As each block is linked to the previous block through its hash value, any modification made to a block will result in a modification of the subsequent blocks, disrupting the entire chain. This also makes it extremely difficult for malicious actors to alter the records without being detected.
Furthermore, the cryptographic nature of hashing algorithms used in blockchain technology ensures that sensitive information remains secure and confidential. By converting data into a fixed-length hash value, blockchain hashing protects the privacy of users and prevents unauthorized access to critical data, reinforcing the security measures inherent in the blockchain.
Several hash algorithms are commonly used in blockchain technology, each with its unique characteristics and applications.
Specific data that has not been altered should always produce the hash value.
In simple terms, validating a hash value is like checking a unique fingerprint for a piece of information. A special code (the hash value) represents a given data included on a block. To make sure the data has not been altered, just recalculate this code and compare it to the original one. If the hash values match, it means the data is still the same and has not been altered, ensuring integrity and security.
Now that we have the theory, let’s delve into the practical aspects of creating and validating a SHA-256 hash, and witness firsthand how to safeguard data.
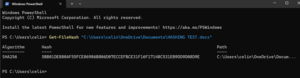
In this example, the SHA256 of the document is 5BB01DE880AF55FCE86986B806D07ECCEFBCE31F16F17148C531EB9DD9D08D9E
Now that the Hash value has been created, we will validate the Hash.
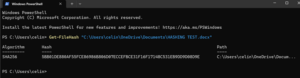
Now let’s check what happens if we modify the document.
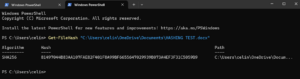
As you can see, the SHA256 of the document is 81497044B83AA107FAE82F401F8A99BF6655647029939B073A4EF3F31C5059B9
Hashing is one of the major components used in blockchain. Understanding the concept is crucial for anyone exploring the complexities of this technology. It not only safeguards the integrity of data stored within each block but also safeguards the entire network against unauthorized alterations.